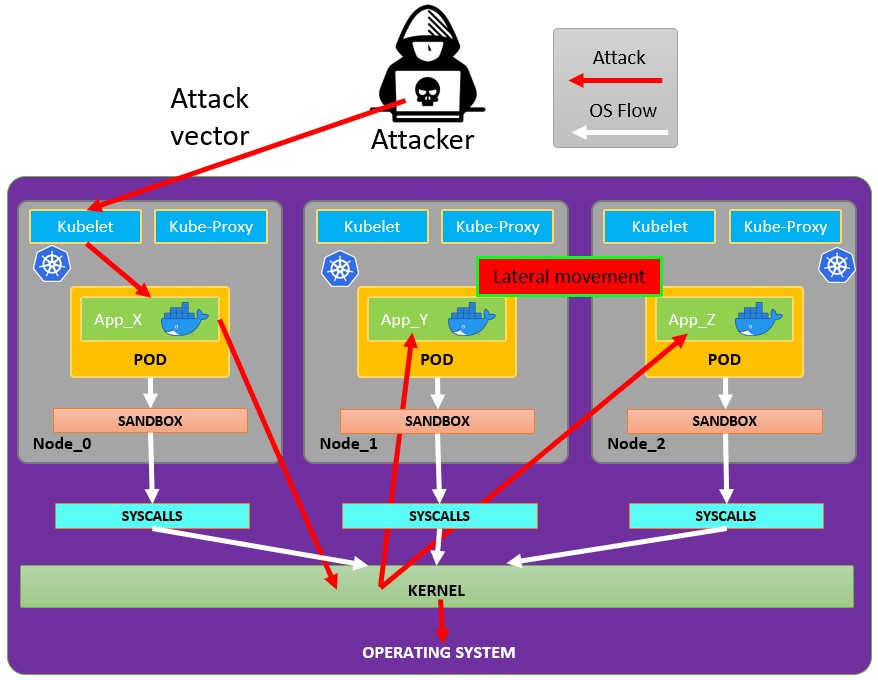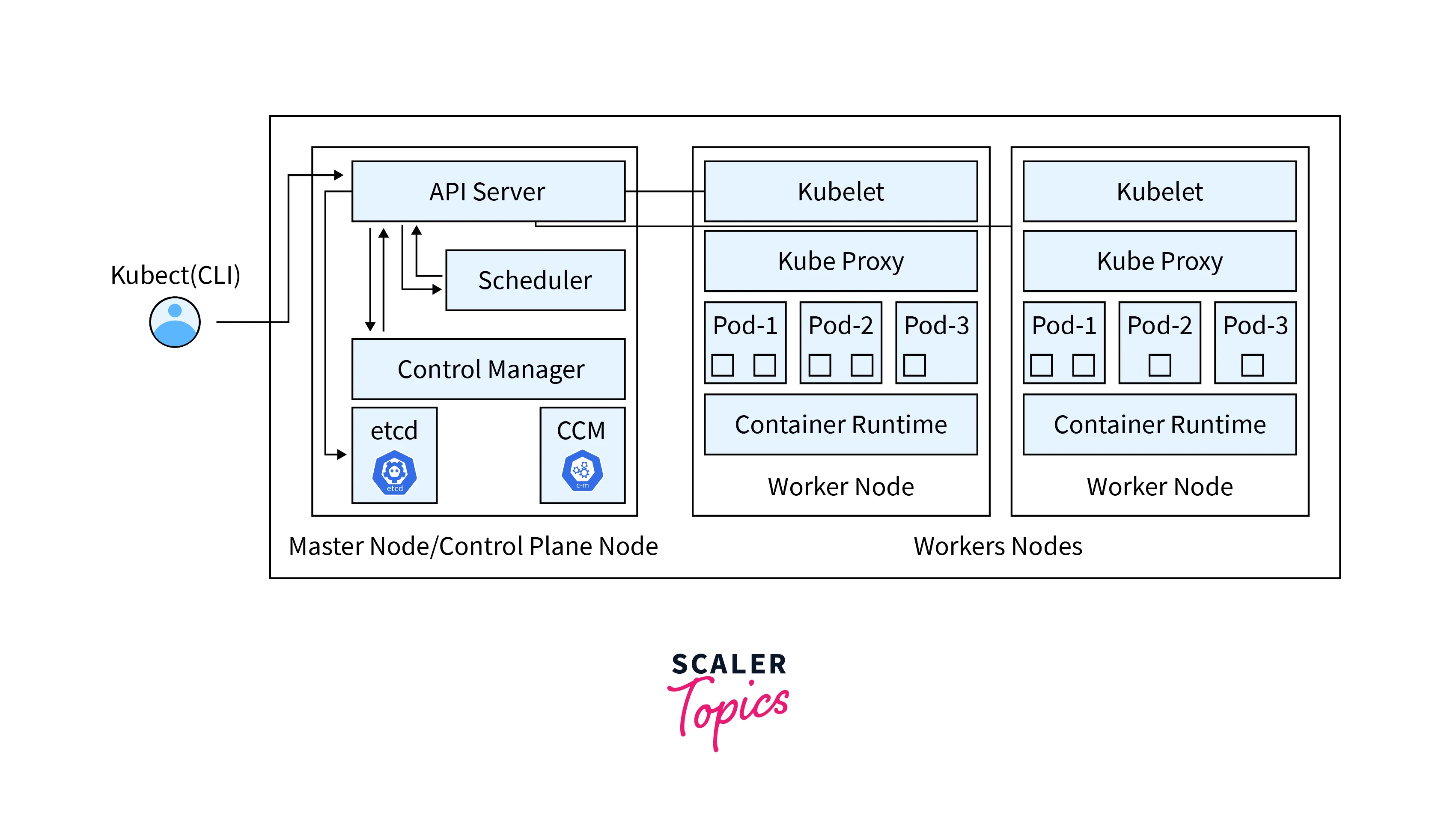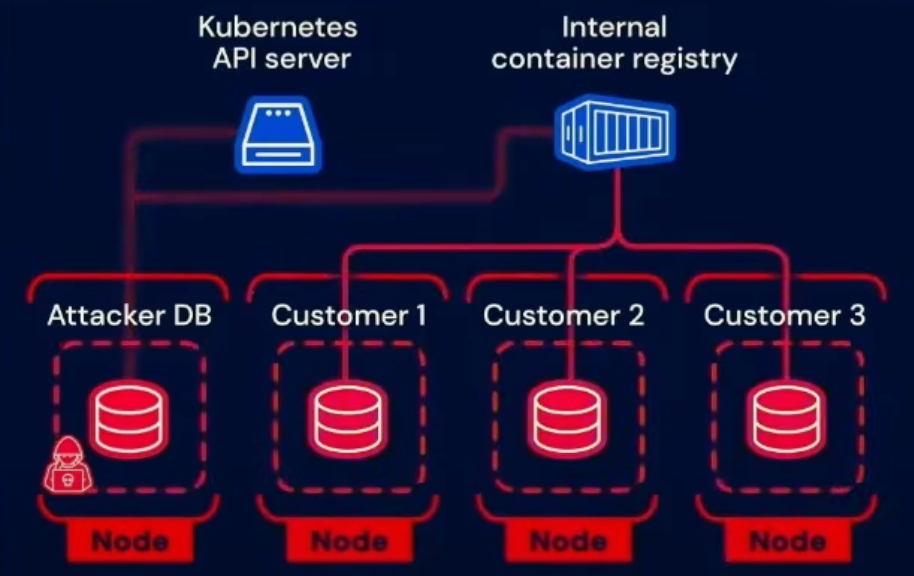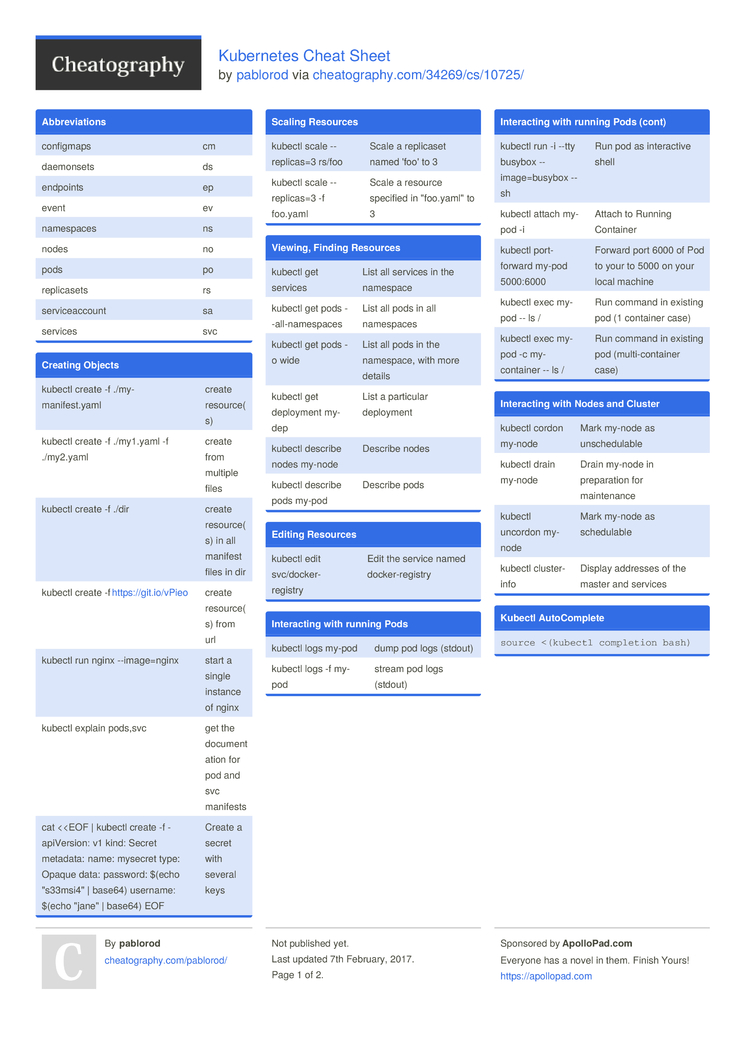
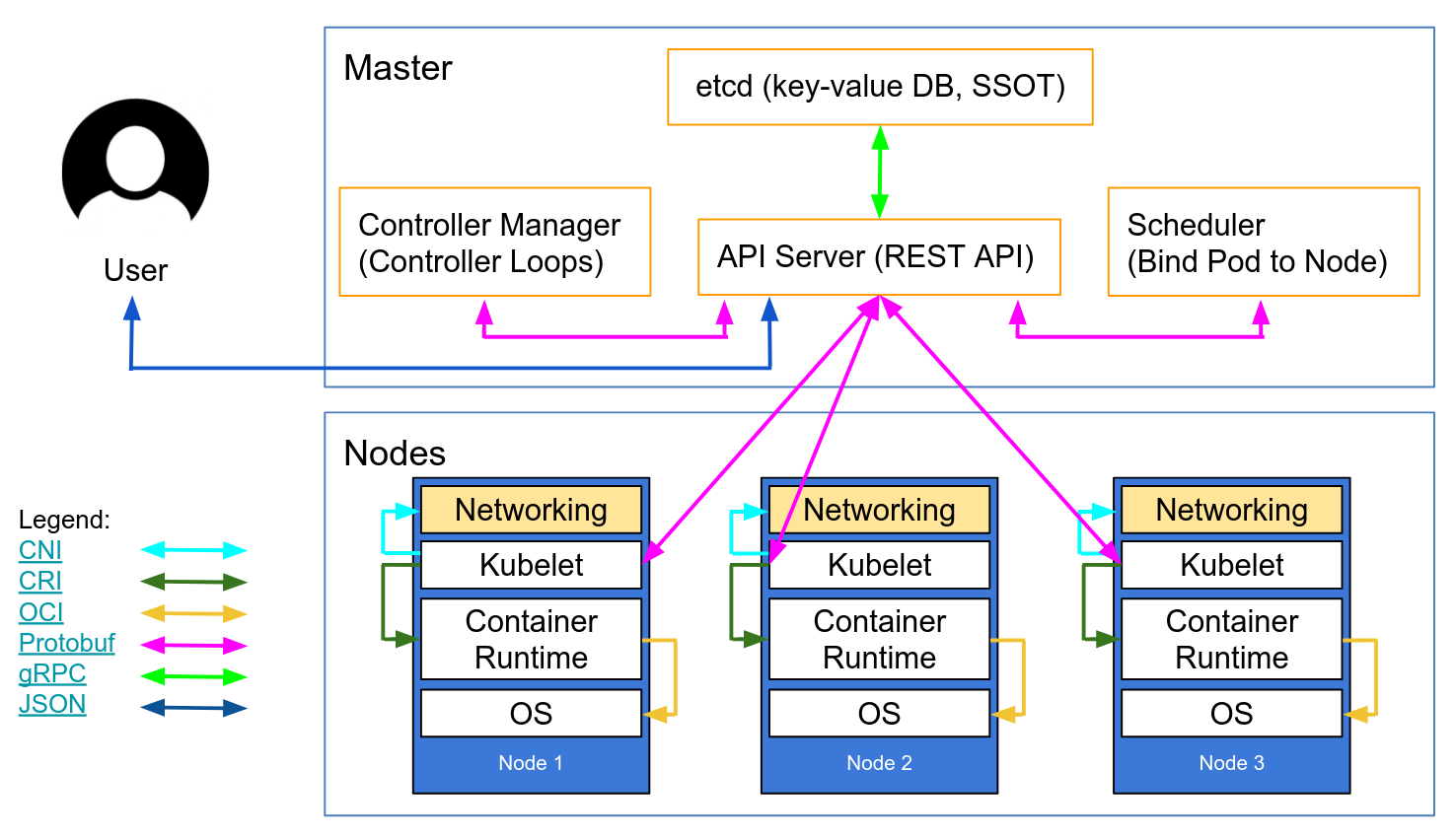
Kubernetes Cheat Sheet by pablorod - Download free from Cheatography - Cheatography.com: Cheat Sheets For Every Occasion
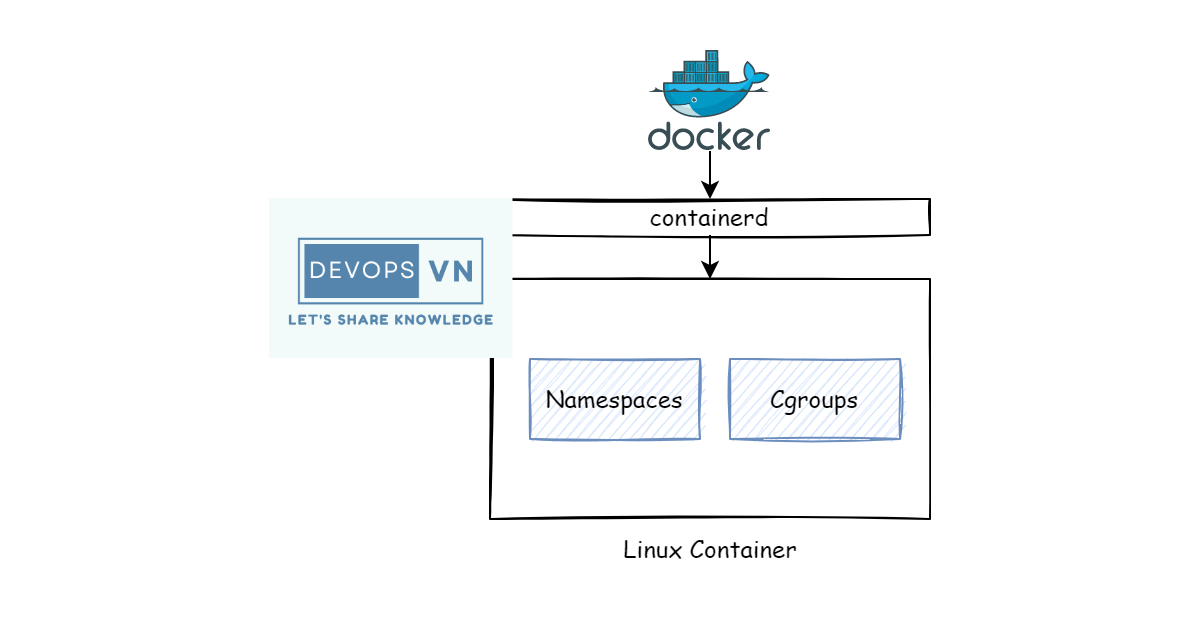
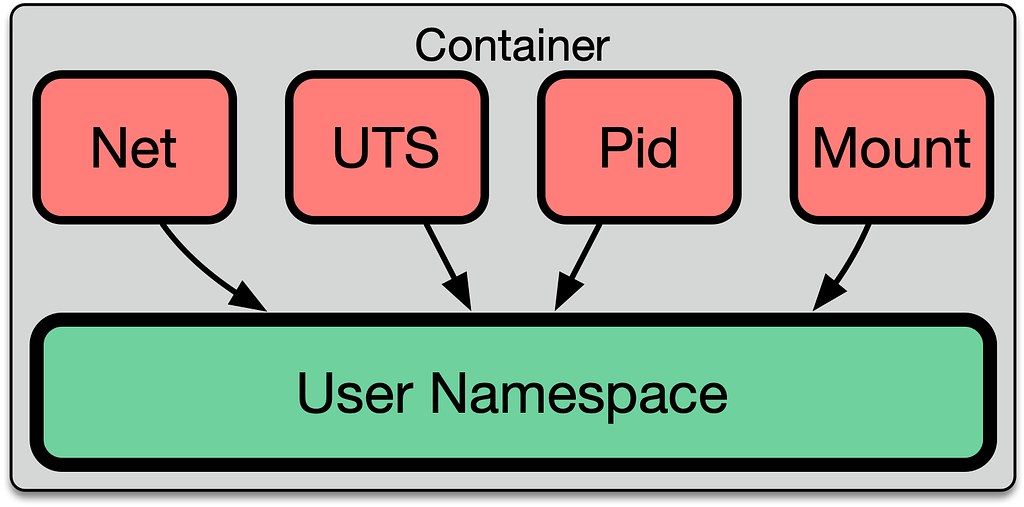
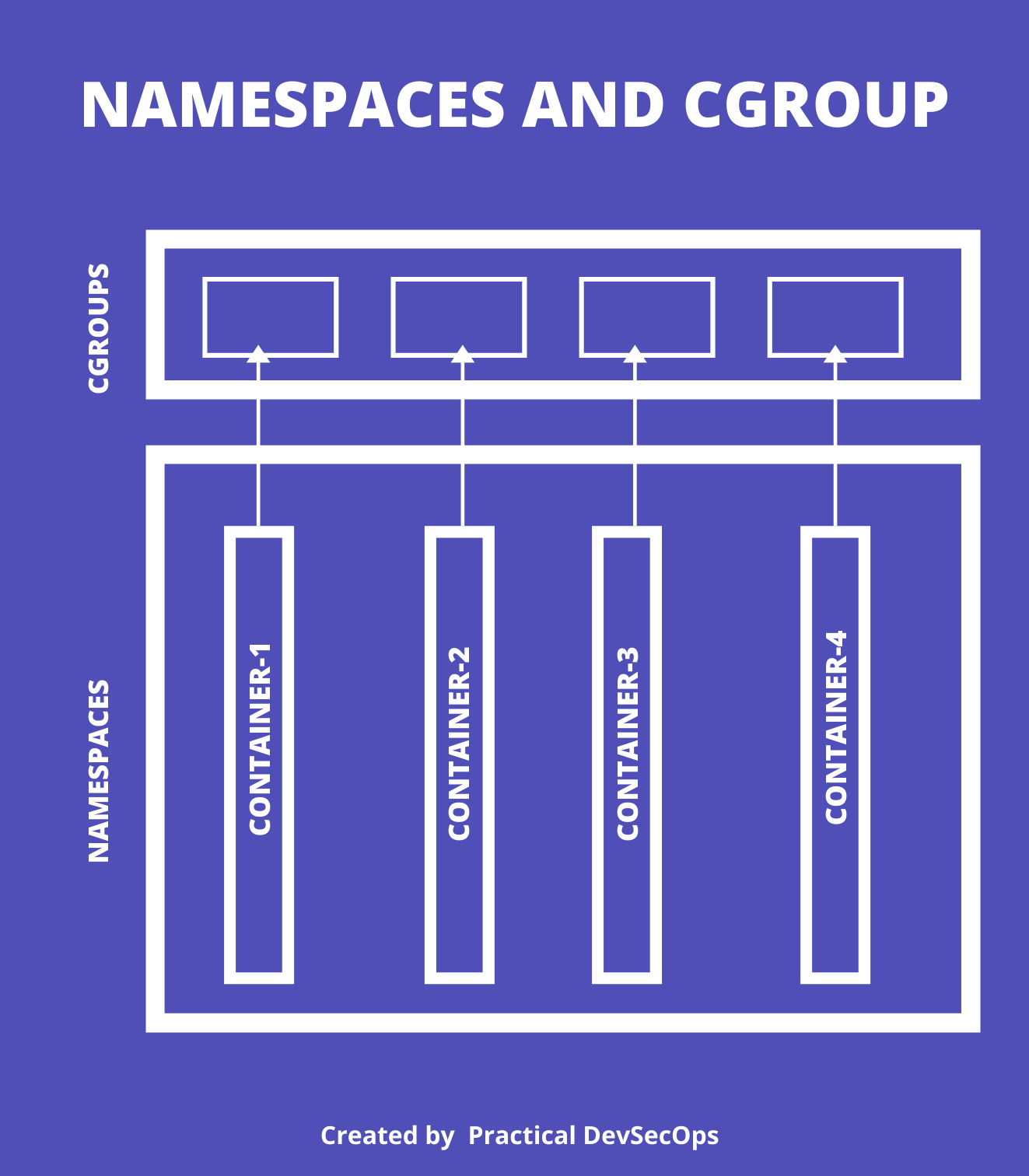
Deep into Container — Linux Namespaces and Cgroups: What are containers made from? | by Quân Huỳnh | FAUN — Developer Community 🐾



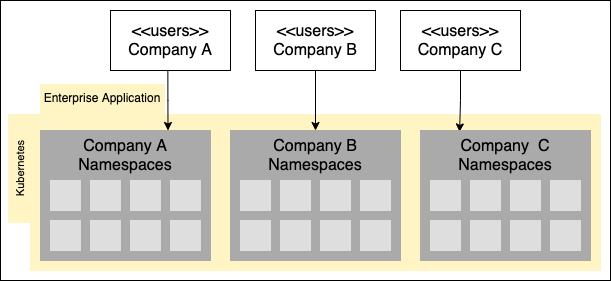




.webp)