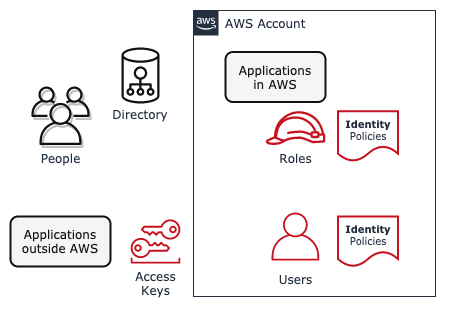
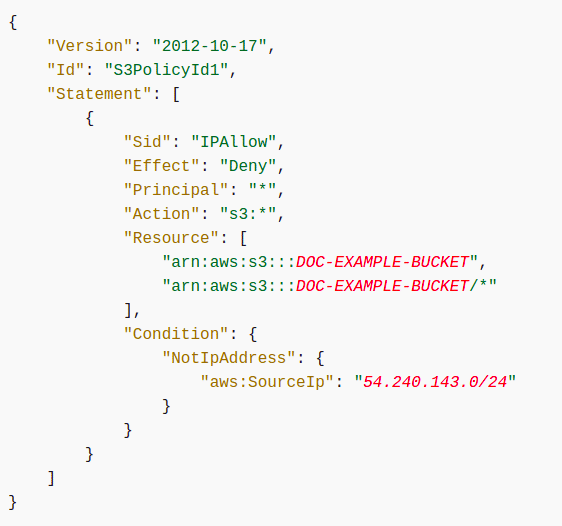
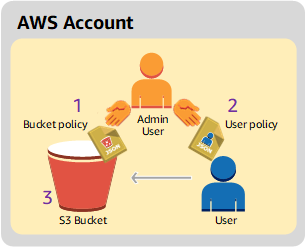
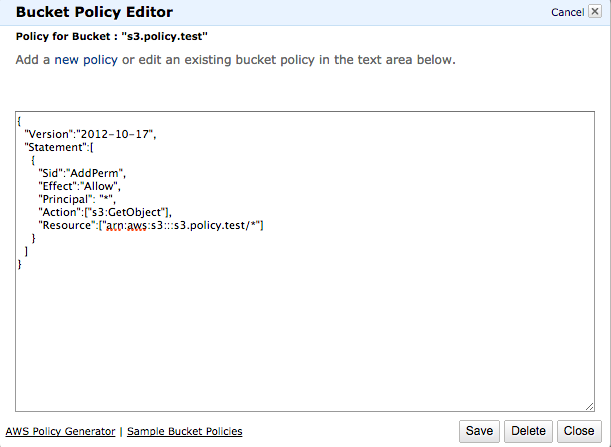
IAM makes it easier for you to manage permissions for AWS services accessing your resources | AWS Security Blog

amazon web services - AWS - InvalidAccessKeyId returned when accessing S3 bucket via CloudFront HTTPS distribution - Stack Overflow

S3 bucket policy invalid principal for cloudfront · Issue #10158 · hashicorp/terraform-provider-aws · GitHub
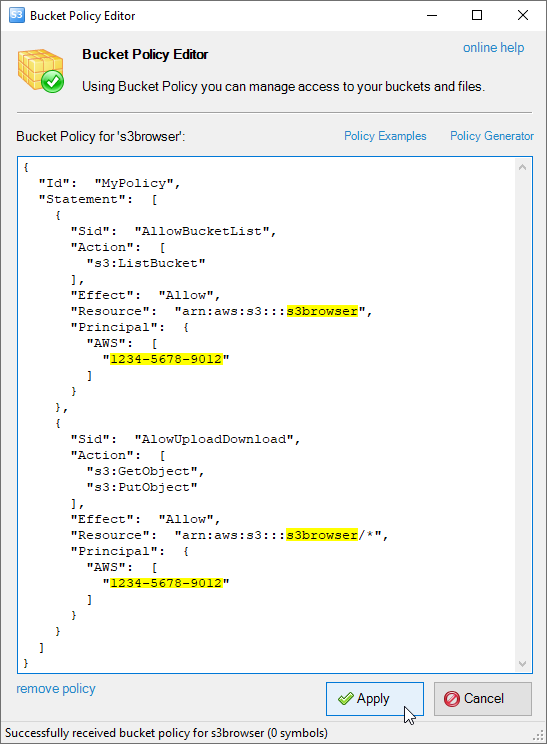
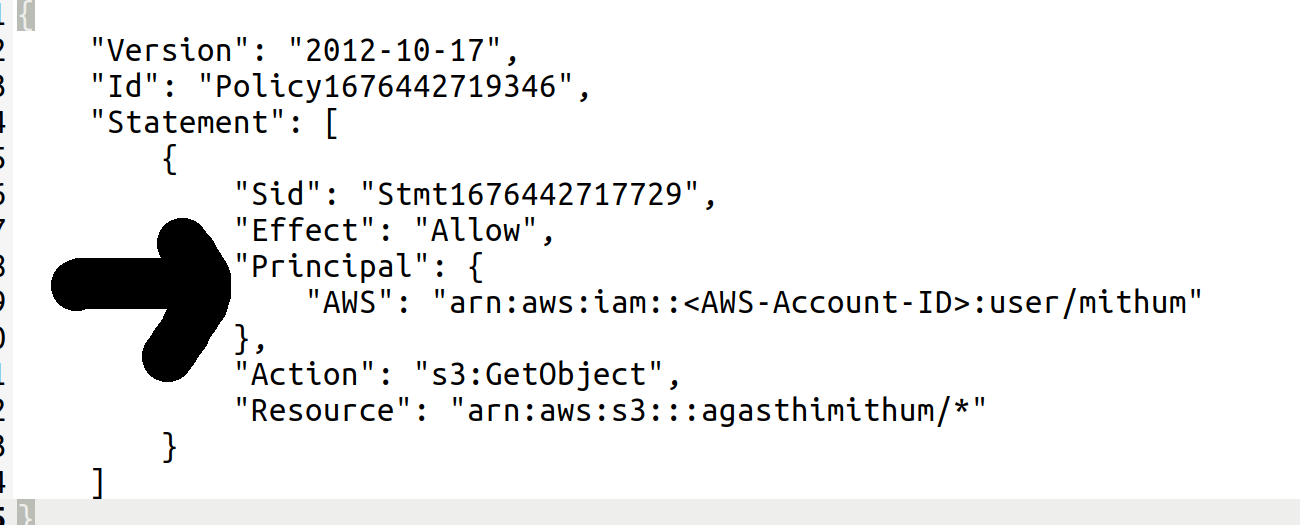
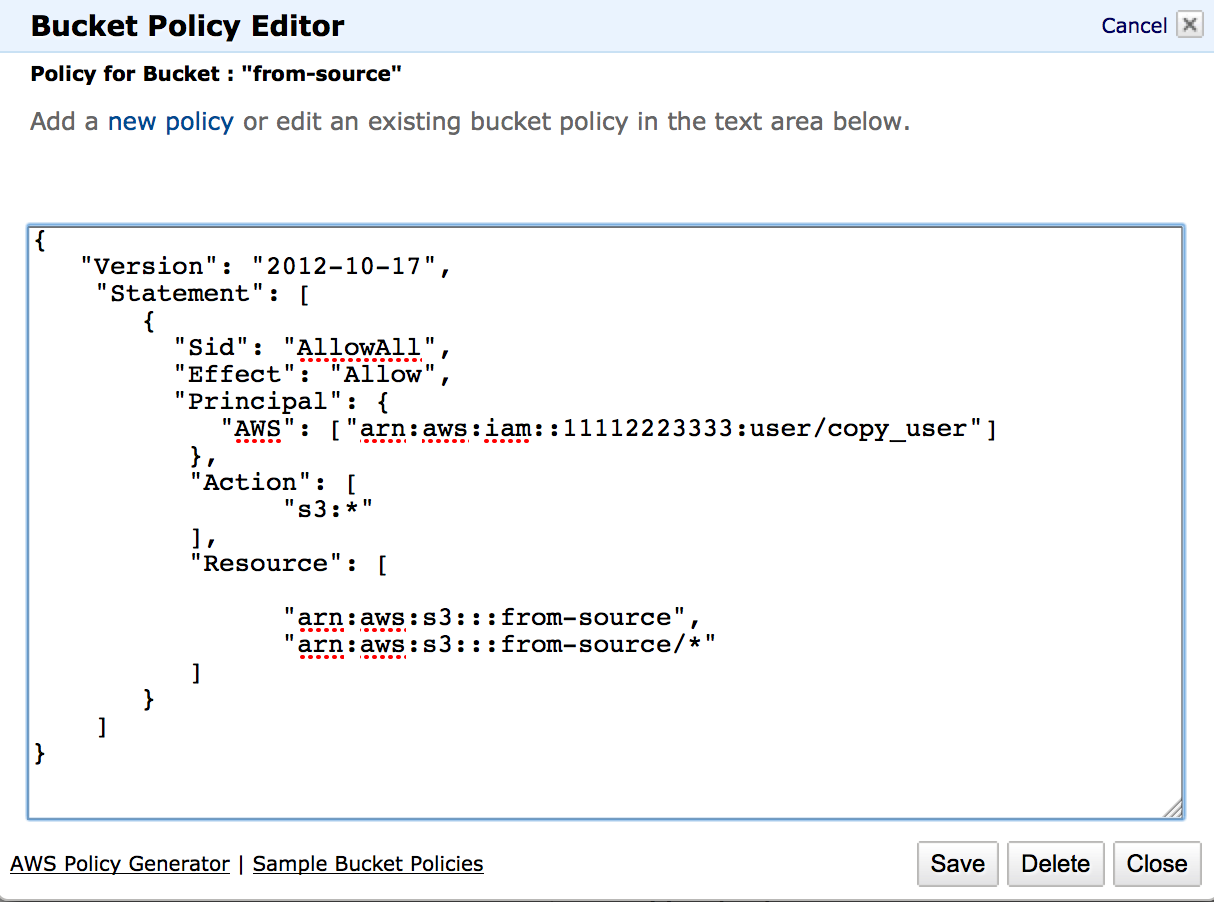
Bucket Sharing Tutorial. How to share Amazon S3 Bucket with another AWS Account. How to grant access to your bucket.

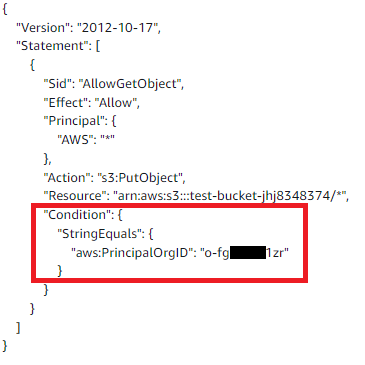
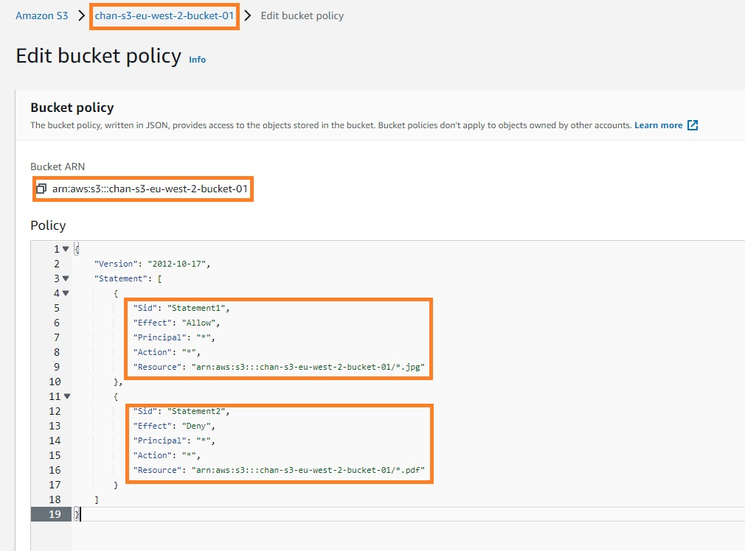
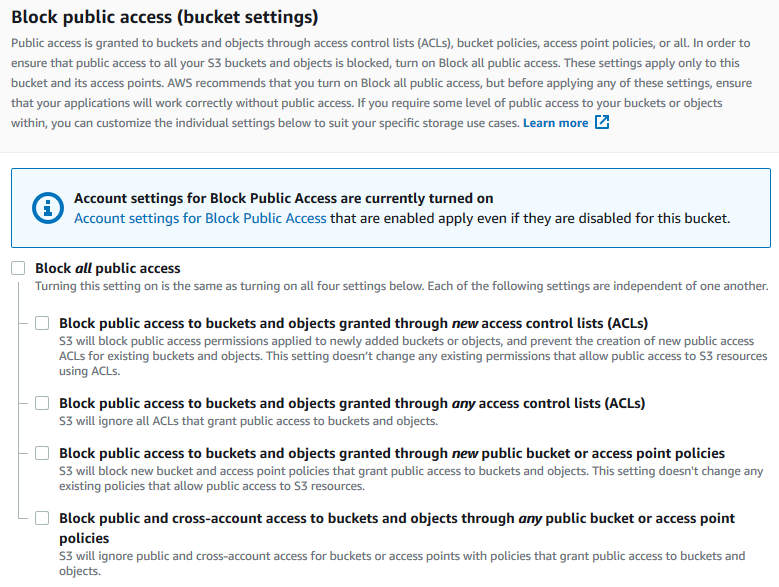
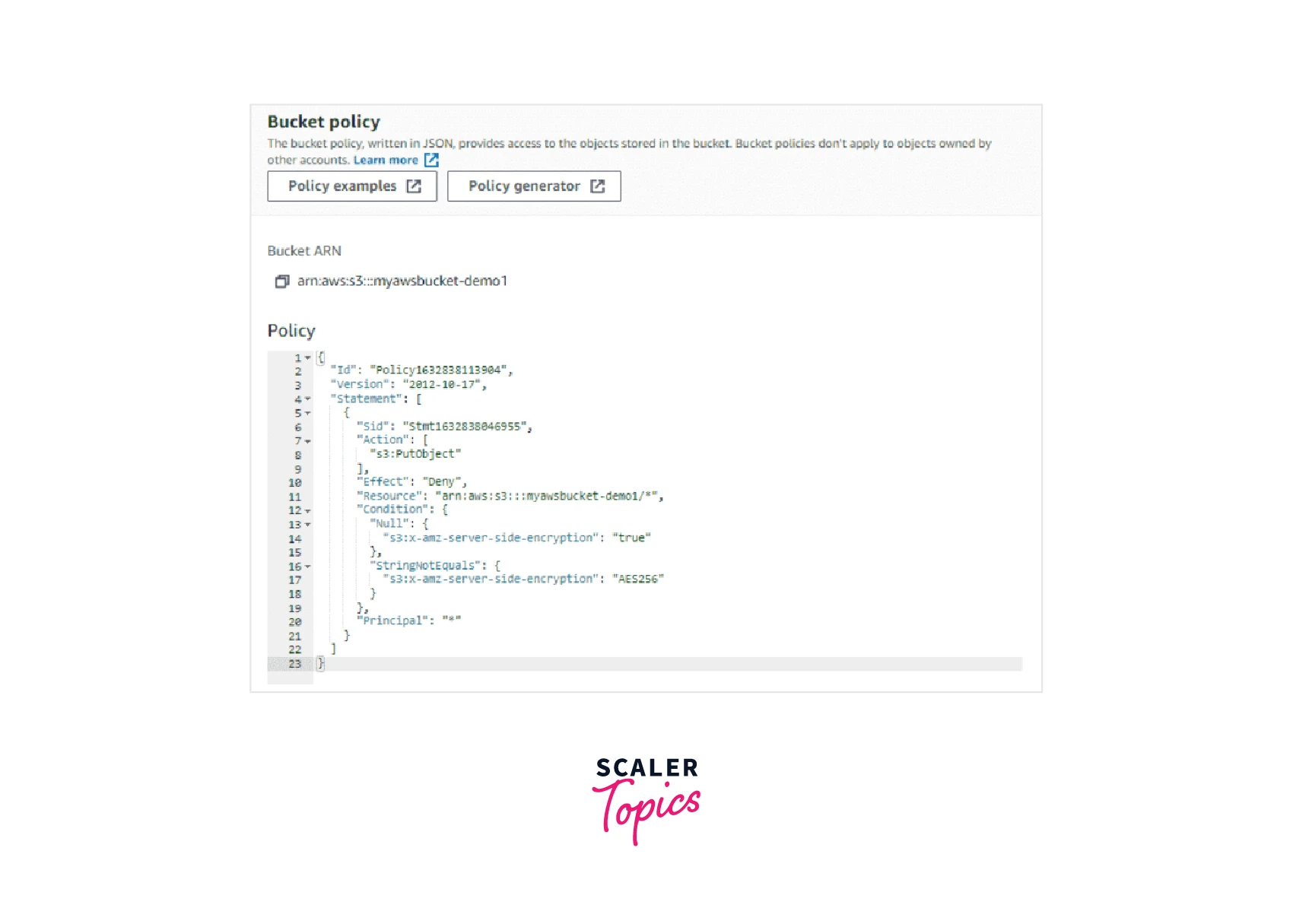
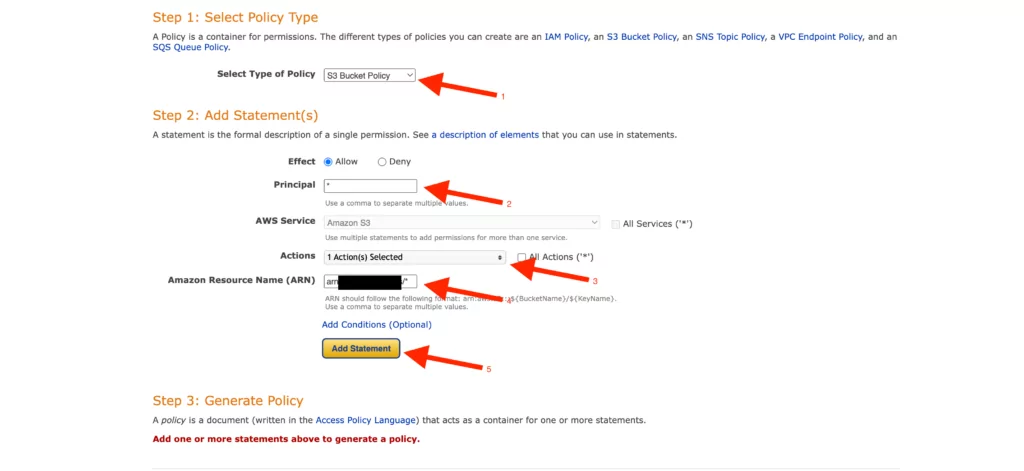
Validate access to your S3 buckets before deploying permissions changes with IAM Access Analyzer | AWS Security Blog